Integrations
Getting started with Integrations
What are Integrations in Tidal Control?
Integrations enable Tidal Control to connect with external systems and tools for real-time compliance monitoring. By configuring integrations, external tests can automatically retrieve data from your existing IT infrastructure.
Core functionalities:
- Real-time data retrieval from external systems for compliance validation
- Automatic compliance tests based on actual system configurations
- Centralized monitoring of distributed IT infrastructure
- Objective compliance measurements without manual data collection
- Continuous compliance monitoring instead of periodic audits
Integrations vs manual compliance controls
Integrations are ideal for:
- Technical configuration validation (encryption, access control)
- Real-time security baseline monitoring
- Automatic collection of compliance evidence
- Large-scale infrastructure compliance monitoring
Manual controls remain necessary for:
- Procedural compliance (training, awareness)
- Qualitative assessments (policy effectiveness)
- Business process evaluations
- Strategic compliance decisions
Navigating the Integrations overview page
The Integrations page in Settings shows all available external system connections and your current configuration status.
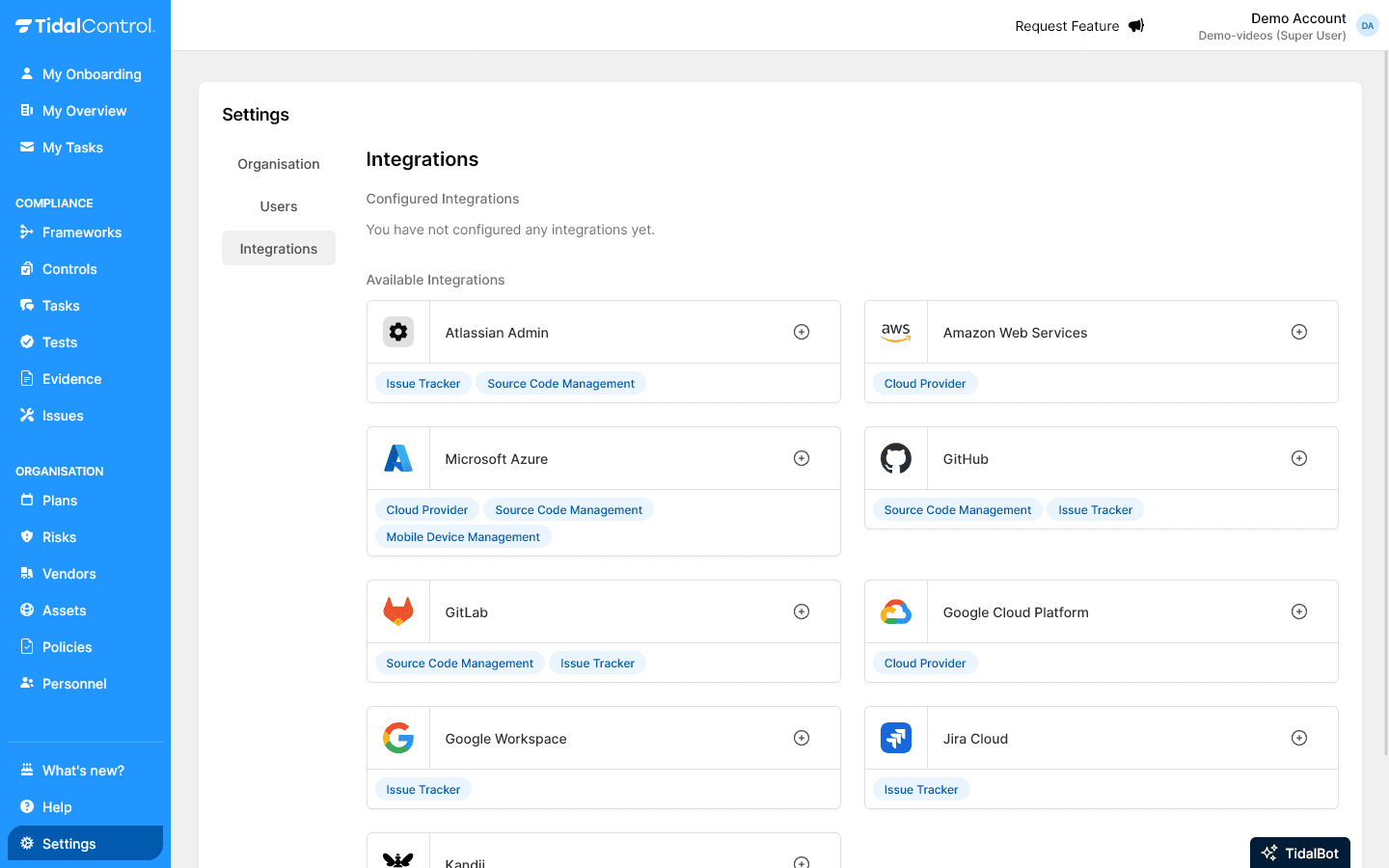
What you see in the overview:
- Configured Integrations - Active integrations already set up
- Available Integrations - Available systems for new connections
- Integration tiles - Visual cards per external system
Configured vs Available Integrations
Configured Integrations section:
- Active connections already set up and working
- Test execution possible via these integrations
Available Integrations section:
- Available systems for new connections
- Click the plus icon to configure integrations for use
Initial setup status:
"You have not configured any integrations yet."
This means you haven't connected any external systems yet and all integrations are still available for configuration.
Understanding available integrations
Cloud Platform Integrations
Amazon Web Services (AWS):
- Security baseline compliance monitoring
- IAM configuration validation
- Encryption settings verification
- Network security group compliance
Microsoft Azure:
- Azure Security Center integration
- Azure Active Directory configuration checks
- Azure Policy compliance monitoring
- Resource encryption validation
Google Cloud Platform:
- Cloud Security Command Center integration
- Identity and Access Management monitoring
- Cloud Resource Manager compliance
- Security configuration baseline checks
Development Platform Integrations
GitHub:
- Repository security settings monitoring
- Branch protection rule compliance
- Code scanning results integration
- Dependency vulnerability tracking
GitLab:
- Project security configuration validation
- CI/CD pipeline security compliance
- Container scanning results integration
- License compliance monitoring
Jira Cloud:
- Issue tracking integration for compliance workflows
- Project management compliance monitoring
- Audit trail integration
- Change management process tracking
Workspace and Productivity Integrations
Google Workspace:
- Admin console security settings
- User account management compliance
- Data loss prevention configuration
- Mobile device management settings
Iru:
- macOS device management compliance
- Security policy enforcement monitoring
- Software deployment compliance tracking
- Device security baseline validation
Integration activation process
General activation steps
For each integration, follow a similar process:
- Select integration from Available Integrations section
- Click plus icon to start setup
- Follow configuration wizard for specific integration
- Configure authentication (API keys, OAuth, service accounts)
- Test connectivity to verify operation
Authentication and security
When setting up authentication, pay attention to the following security measures:
- Least privilege principle - Don't give Tidal integration more rights than necessary. It's often sufficient to give Tidal read rights to specific system functionality.
- Encrypted connections to all external systems
- Regular credential rotation according to best practices
Tidal stores credential information securely in a protected 'key vault' and only communicates with encrypted connections.
Suspect credentials are compromised? Change or remove them immediately, and send an email to support@tidalcontrol.com
Integration impact on Tests
How integrations activate Tests
Integration configuration enables external tests:
- Integration becomes active after successful configuration
- External tests become available for that integration
- Tests can retrieve data from connected systems
- Real-time compliance monitoring becomes possible
Read more about using automatic tests.
Next steps
Now that you understand Integrations:
- Identify critical external systems for compliance monitoring
- Prioritize integrations based on business and compliance impact
- Start with one integration to learn the process
- Select specific integration from articles below for detailed setup instructions
For specific integration setup instructions, see the individual articles in this section for each available integration.
- Previous
- Troubleshooting & FAQ
- Next
- Microsoft Azure